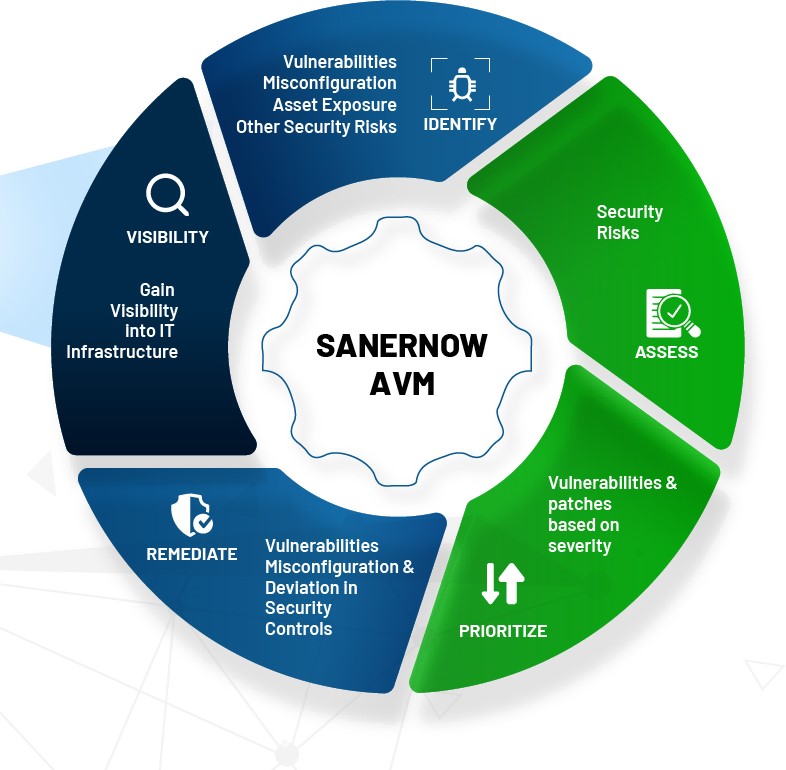
Vulnerability Management Audit Program . Helping you identify, classify, remediate, and mitigate. the objective of this document is bridging the gap in information security by breaking down complex problems into more. What are the differences between a vulnerability, a risk, and a threat? vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as quickly as possible. vulnerability management program framework. If you are a manager or ciso, the. learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust.
from www.secpod.com
a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as quickly as possible. learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust. Helping you identify, classify, remediate, and mitigate. vulnerability management program framework. the objective of this document is bridging the gap in information security by breaking down complex problems into more. If you are a manager or ciso, the. What are the differences between a vulnerability, a risk, and a threat? vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,.
The Most Effective Vulnerability Assessment Framework to Keep your
Vulnerability Management Audit Program the objective of this document is bridging the gap in information security by breaking down complex problems into more. learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust. the objective of this document is bridging the gap in information security by breaking down complex problems into more. vulnerability management program framework. If you are a manager or ciso, the. vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as quickly as possible. Helping you identify, classify, remediate, and mitigate. What are the differences between a vulnerability, a risk, and a threat?
From blog.convisoappsec.com
Vulnerability Management Process, what is it? Conviso AppSec Vulnerability Management Audit Program the objective of this document is bridging the gap in information security by breaking down complex problems into more. Helping you identify, classify, remediate, and mitigate. If you are a manager or ciso, the. vulnerability management program framework. learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust.. Vulnerability Management Audit Program.
From www.kratikal.com
How is Vulnerability Management Different from Vulnerability Assessment Vulnerability Management Audit Program What are the differences between a vulnerability, a risk, and a threat? the objective of this document is bridging the gap in information security by breaking down complex problems into more. vulnerability management program framework. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as. Vulnerability Management Audit Program.
From www.secpod.com
The Most Effective Vulnerability Assessment Framework to Keep your Vulnerability Management Audit Program a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as quickly as possible. vulnerability management program framework. the objective of this document is bridging the gap in information security by breaking down complex problems into more. vulnerability management is a continuous, proactive, and often. Vulnerability Management Audit Program.
From brightsec.com
Vulnerability Management Lifecycle, Tools, and Best Practices Vulnerability Management Audit Program If you are a manager or ciso, the. vulnerability management program framework. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as quickly as possible. What are the differences between a vulnerability, a risk, and a threat? Helping you identify, classify, remediate, and mitigate. vulnerability. Vulnerability Management Audit Program.
From s4applications.uk
Vulnerability Management Programme And Dashboards S4 Applications Vulnerability Management Audit Program What are the differences between a vulnerability, a risk, and a threat? learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust. If you are a manager or ciso, the. Helping you identify, classify, remediate, and mitigate. a strong vulnerability management program uses threat intelligence and knowledge of it. Vulnerability Management Audit Program.
From www.esecforte.com
Vulnerability Assessment Scanning Tools List 2018 eSecForte Vulnerability Management Audit Program What are the differences between a vulnerability, a risk, and a threat? vulnerability management program framework. learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust. vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. a strong vulnerability management program. Vulnerability Management Audit Program.
From www.pandasecurity.com
What is a Vulnerability Assessment? Panda Security Vulnerability Management Audit Program Helping you identify, classify, remediate, and mitigate. vulnerability management program framework. What are the differences between a vulnerability, a risk, and a threat? learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust. vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems,. Vulnerability Management Audit Program.
From www.securitynewspaper.com
How to do security vulnerability testing? Vulnerability Management Audit Program the objective of this document is bridging the gap in information security by breaking down complex problems into more. If you are a manager or ciso, the. vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. learn what vulnerability management is, what steps are involved in the process, and how. Vulnerability Management Audit Program.
From www.crowdstrike.com
What is Vulnerability Management? CrowdStrike Vulnerability Management Audit Program If you are a manager or ciso, the. vulnerability management program framework. What are the differences between a vulnerability, a risk, and a threat? Helping you identify, classify, remediate, and mitigate. the objective of this document is bridging the gap in information security by breaking down complex problems into more. a strong vulnerability management program uses threat. Vulnerability Management Audit Program.
From sysdig.com
Top vulnerability assessment and management best practices Sysdig Vulnerability Management Audit Program If you are a manager or ciso, the. the objective of this document is bridging the gap in information security by breaking down complex problems into more. vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. What are the differences between a vulnerability, a risk, and a threat? learn what. Vulnerability Management Audit Program.
From www.spiceworks.com
What Is Vulnerability Management? Definition, Lifecycle, Policy, and Vulnerability Management Audit Program What are the differences between a vulnerability, a risk, and a threat? the objective of this document is bridging the gap in information security by breaking down complex problems into more. vulnerability management program framework. Helping you identify, classify, remediate, and mitigate. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations. Vulnerability Management Audit Program.
From www.pandasecurity.com
What is a Vulnerability Assessment? Panda Security Vulnerability Management Audit Program learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust. vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. the objective of this document is bridging the gap in information security by breaking down complex problems into more. What are the. Vulnerability Management Audit Program.
From www.g2.com
What Is Vulnerability Management? Why Does It Matter? Vulnerability Management Audit Program learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust. the objective of this document is bridging the gap in information security by breaking down complex problems into more. vulnerability management program framework. a strong vulnerability management program uses threat intelligence and knowledge of it and business. Vulnerability Management Audit Program.
From www.businesstechweekly.com
Vulnerability Assessments 4 Crucial Steps for Identifying Vulnerability Management Audit Program Helping you identify, classify, remediate, and mitigate. vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. What are the differences between a vulnerability, a risk, and a threat? vulnerability management program framework. learn what vulnerability management is, what steps are involved in the process, and how you can implement a. Vulnerability Management Audit Program.
From www.balbix.com
Vulnerability Management Program How to Built It? Balbix Vulnerability Management Audit Program learn what vulnerability management is, what steps are involved in the process, and how you can implement a robust. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as quickly as possible. If you are a manager or ciso, the. What are the differences between a. Vulnerability Management Audit Program.
From zsecurity.org
Creating a Vulnerability Management Strategy zSecurity Vulnerability Management Audit Program the objective of this document is bridging the gap in information security by breaking down complex problems into more. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as quickly as possible. learn what vulnerability management is, what steps are involved in the process, and. Vulnerability Management Audit Program.
From www.balbix.com
Vulnerability Management Framework Balbix Vulnerability Management Audit Program If you are a manager or ciso, the. vulnerability management program framework. Helping you identify, classify, remediate, and mitigate. a strong vulnerability management program uses threat intelligence and knowledge of it and business operations to prioritize risks and address vulnerabilities as quickly as possible. learn what vulnerability management is, what steps are involved in the process, and. Vulnerability Management Audit Program.
From s4applications.uk
Vulnerability Management Programme And Dashboards S4 Applications Vulnerability Management Audit Program vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. What are the differences between a vulnerability, a risk, and a threat? Helping you identify, classify, remediate, and mitigate. If you are a manager or ciso, the. the objective of this document is bridging the gap in information security by breaking down. Vulnerability Management Audit Program.